AI-assisted threat hunting – from cloud and data center workloads to the enterprise
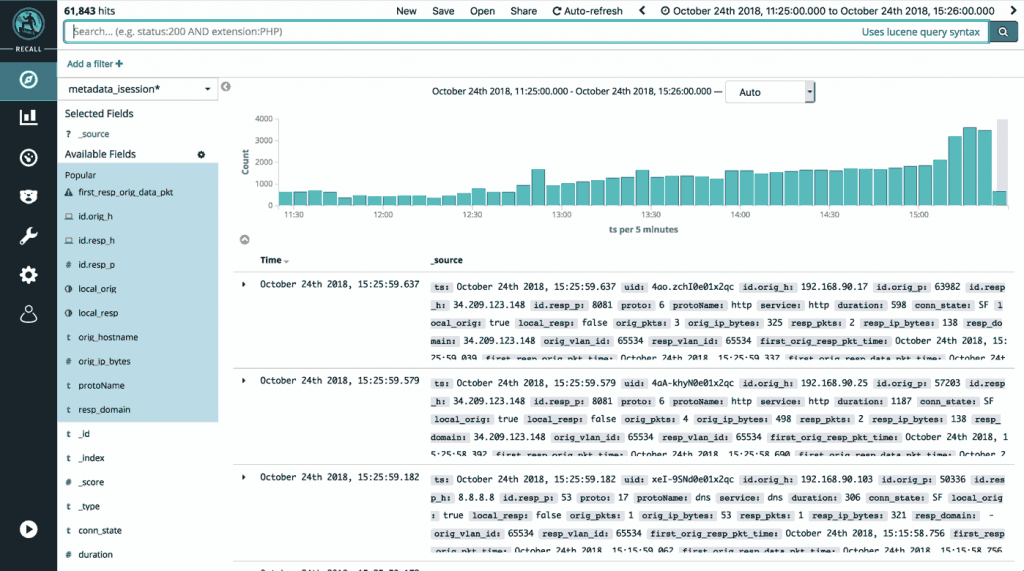

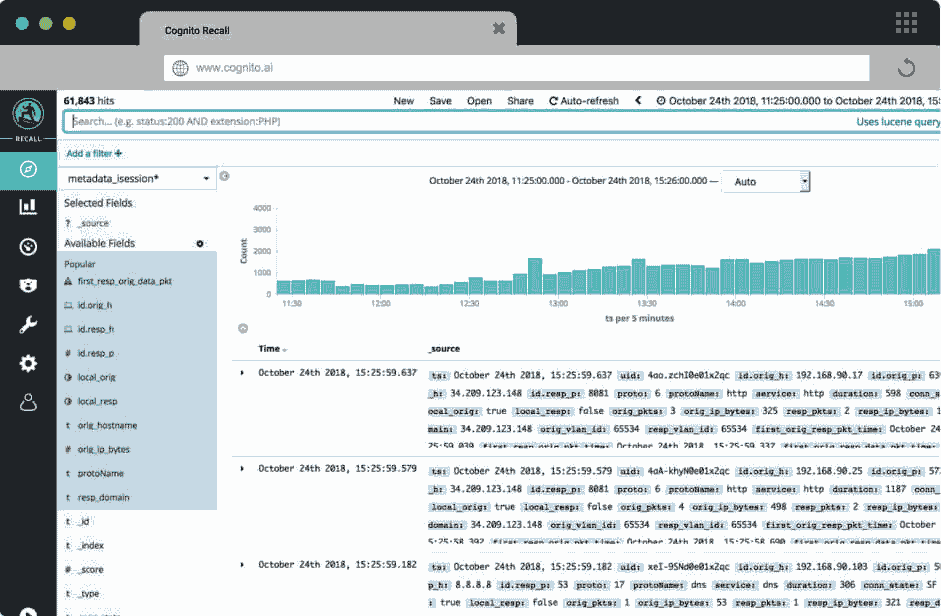
Cognito Recall is a dramatic leap forward in AI-assisted threat hunting and incident investigation"
Mark Rodman
Head of Information Security Operations at PokerStars
The Stars Group, Owner of PokerStars, the World’s Largest Online Poker Site
Think about your data capture and analysis architecture and deployment. We invite you to reach out to a Tempest Telecom representative for a consultative discussion about your deployment.