See and stop what matters with AI powered network detection and response
Account takeover in Office 365 has become the largest threat vector in the cloud

Rise in compromised credentials to email accounts

Cloud security failures in the customer’s portion of the responsibility model

Breaches taking months or longer to discover
Multifactor authentication (MFA), cloud access security brokers and email security all fail, here’s how:
Attackers can already steal authenticated sessions, even those protected by MFA.
Attackers move across cloud service providers, SaaS and your entire workforce, blindsiding Cloud Access Security Brokers (CASB).
Email filtering and anti-phishing struggles with targeted and unknown attacks.
30% of organizations suffer account takeovers every month, even with multifactor authentication. By understanding attacker behaviors and account privilege, Vectra puts an end to account takeovers.
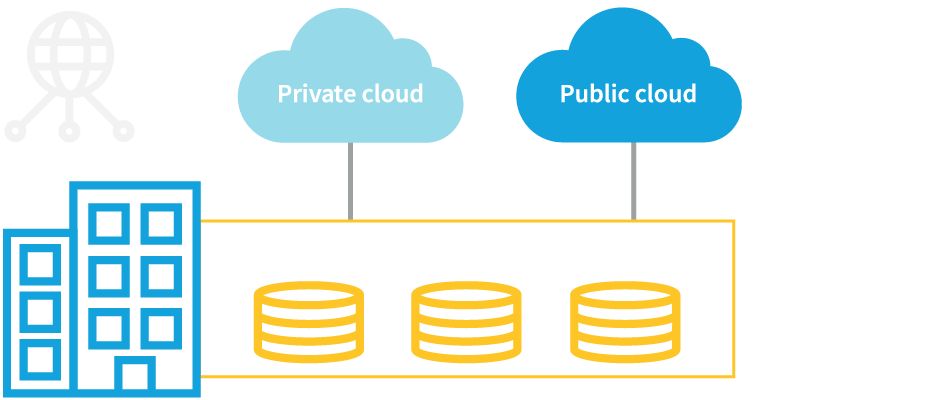
Attackers don’t operate in silos. Your security solution shouldn’t either. Vectra tracks attacker activity that pivots between enterprise, data center, IaaS and SaaS. All from a single place.
Vectra AI-driven threat detection finds attackers who are in your environment and past the preventative security defenses, such as firewalls and CASBs.
Widespread threat coverage – Stop data breaches by detecting threats in Office 365 and leveraging AI to identify malicious behaviors and hijacked accounts.
Deploy in minutes with a cloud-native approach that quickly starts to monitor, detect and stop attacks.
Regain comprehensive security coverage between Office 365 and your local enterprise infrastructure.
Stop unknown and known attacks and account takeovers in real time before they lead to data breaches.
Attackers user Power Automate to:
Bypasses DLP and other security controls
